 Security
Security1Password Introduces Pop-up Warnings for Suspected Phishing Sites
1Password adds pop-up warnings to protect users from suspected phishing sites, enhancing its digital vault and password management security.
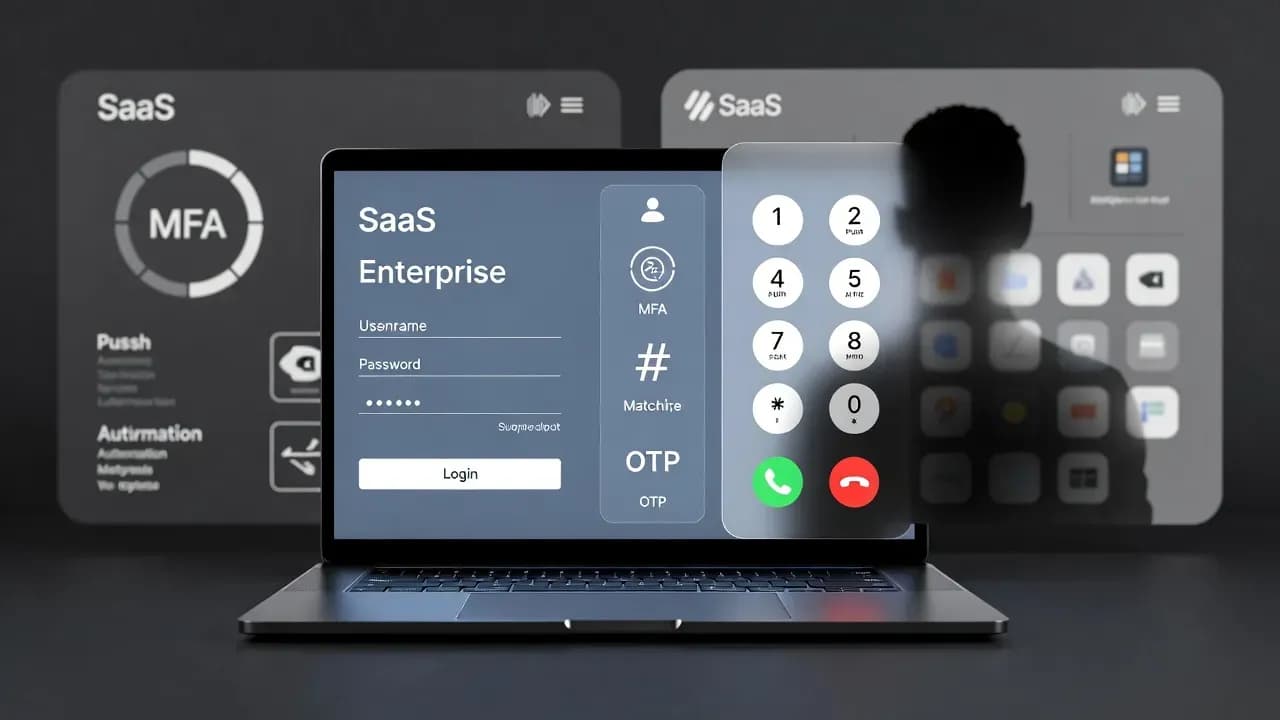
Okta is warning about custom vishing-focused phishing kits sold "as-a-service" that let attackers or...
3 days ago
Pwn2Own Automotive 2026 delivered a blunt message to anyone operating modern vehicle ecosystems: the...
3 days ago
A newly disclosed critical vulnerability in GNU InetUtils telnetd is already being exploited in the...
3 days ago
The VS Code extension ecosystem is now a frontline supply chain target. Researchers uncovered two AI...
3 days ago
CISA's latest KEV additions highlight a pattern security teams cannot ignore: attackers are blending...
3 days ago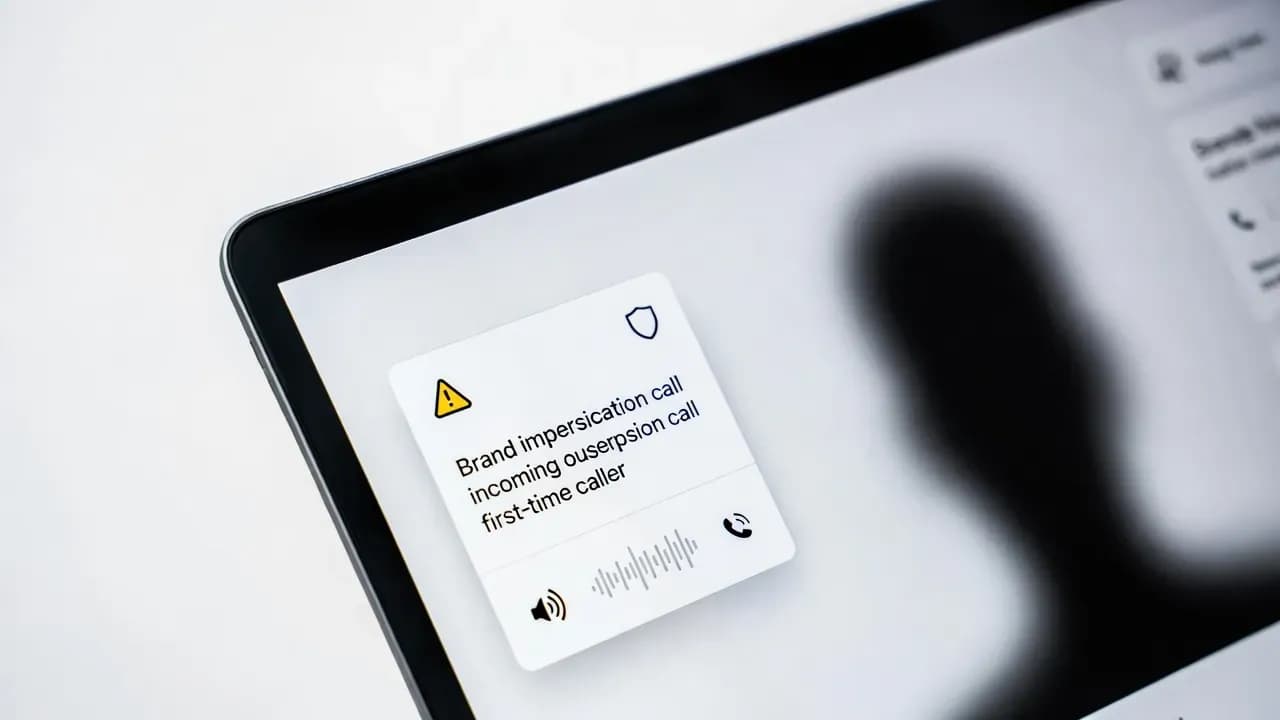
Vishing has shifted from random robocalls to targeted, scripted attacks that exploit trust in famili...
3 days ago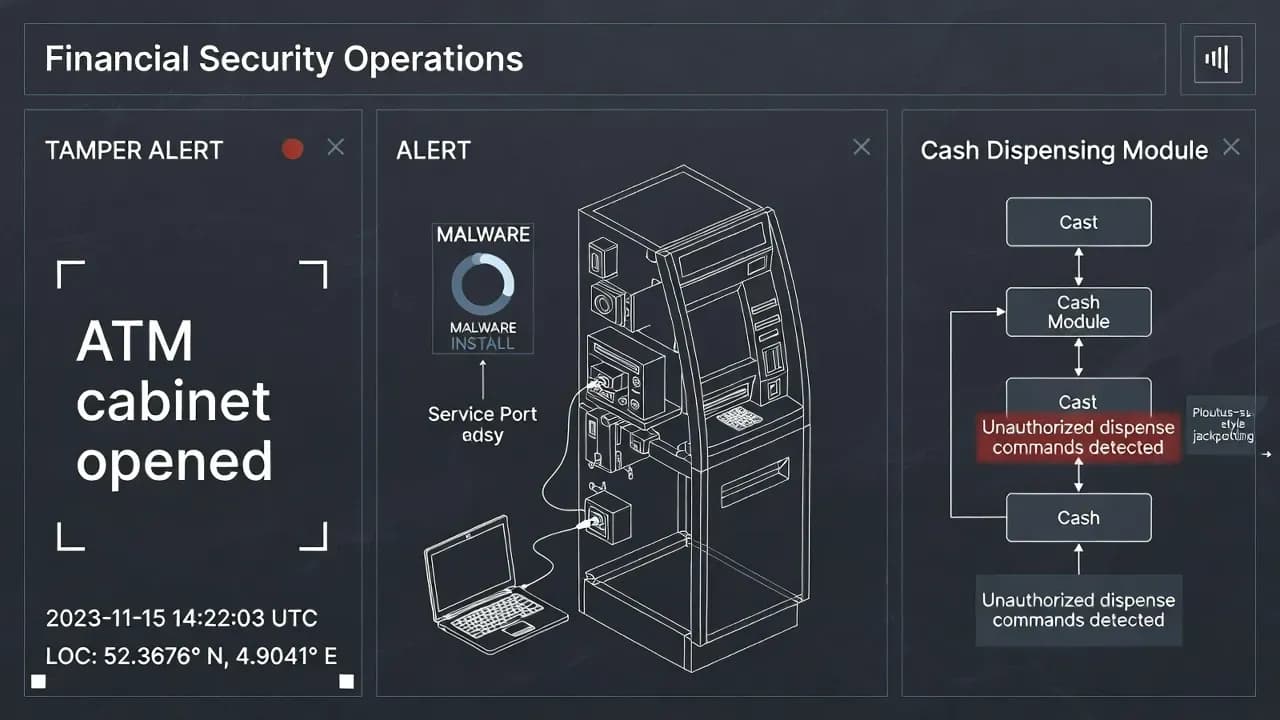
Federal authorities are moving to deport Venezuelan nationals convicted of orchestrating ATM jackpot...
3 days ago
Microsoft has published a temporary workaround for classic Outlook freezing after January 2026 Windo...
3 days ago






Anavem delivers breaking cybersecurity news, in-depth tutorials, and practical IT tools for professionals. Stay informed about the latest vulnerabilities, software updates, and security best practices. Whether you're managing Windows Server environments, automating with PowerShell, or implementing Zero Trust architecture, we provide the resources you need to excel in IT.